Knowing how to keep your web traffic data safe while browsing the web on unknown networks is a vital skill that not enough savvy Internet surfers take part in. I have previously discussed a few ways of solving this issue through the use of SSH tunnels (manually-created and application managed). I have also discussed things like "anonymous" web browsing through the Janus Privacy Adapter as well as with public Tor nodes. (Side note: Anonymous in quotes because truly anon browsing requires encrypted, signed traffic over private Tor networks — not public, published ones everyone knows about — but I digress). While VPN is nothing new and has been used by businesses and their employees for over a decade, it has not generally been something aimed at the typical Internet user. However, there is a problem with all of these solutions — they are just too hard to setup for most users and have various drawbacks (see nerd talk at the end of this post).
Enter VyprVPN

A recently launched software development company called Golden Frog, inspired by the creators of Giganews, debuted their VPN service called VyprVPN. Having been a happy customer of Giganews for the last 2 years and therefore receiving access to VyprVPN in my account, I decided to put their claims to the test with this review.
VyprVPN provides a secure encrypted connection to the Internet, creating a solid layer of online privacy protection unavailable with traditional Internet security software. Valued at 14.99 per month, VyprVPN is free to Diamond customers for a limited time.
Before beginning with setup and my VyprVPN review, let's see how it is marketed to get a better idea of its uses. Golden Frog mentions VyprVPN in the context of privacy, security, reliability & speed, as well as trust and stability. I'll try to summarize what they're aiming for briefly:
"VyprVPN thwarts Deep Packet Inspection by encrypting your Internet traffic as it passes through your ISP."
"You get a high-speed connection with unlimited speed. VyprVPN has the bandwidth and high-quality server infrastructure to deliver 99.99% uptime."
"VyprVPN was developed by Golden Frog, a global software developer which is currently partnering with Giganews to beta the service for free with Giganews' Usenet customers."
What You Should Not Use VyprVPN For
I feel obligated to mention that using VyprVPN in an attempt to hide your tracks while doing nefarious online activities is not a good idea. I say "attempting to hide your tracks" because a quick read of the Golden Frog VyprVPN Privacy Policy and Terms of Service shows that they complies with criminal investigations:
Golden Frog cooperates fully with law enforcement agencies, yet there must still be a subpoena before Golden Frog provides a member's identifying information - minimal information reasonably calculated to identify and no more. In a criminal investigation Golden Frog is required by the Law to not divulge the fact of the investigation to the member.
While on the subject, Golden Frog has a list of prohibited activites while using VyprVPN or any of their services:
Spamming (email, Usenet, message boards, etc.)
Copyright, trademark, and patent infringement.
Defamatory or abusive language
IP Spoofing
Illegal or unauthorized access to other computers or networks
Distribution of Internet viruses, worms, or other destructive activities
Export control violations
All other illegal activities
I just wanted to get that out of the way as there seems to be a consensus among tech-savvy people my age (or at least all my computer science friends have been to one too many Black Hat, DEF CON, HOPE and ShmooCon conventions) that SSH tunnels, Tor networks and VPN services were created solely for hiding their web traffic while doing shady things online. There are in fact real world legitimate uses for VPNs on a daily basis...
What You Can/Should Use VyprVPN For
-
Using inflight Wi-Fi by a provider such as Gogo that uses a completely open and unencrypted Wi-Fi access point with no link layer security. Anyone on the flight could open up a packet sniffer and see what you are up to online.
-
Using similar public Wi-Fi access points at coffee shops, airports, that inviting open access point named "Linksys" that just seems to follow you around or those hotel networks that allow you to see other computers on the network. Or even while on your own GSM 3G data card (but to be honest the chances of having your GSM 3G data packets sniffed are very, very slim as it's not just as easy as any random script kiddie installing Wireshark or NetWitness Investigator)
-
Bypassing your ISP's port blocking and/or traffic shaping and throttling activities based on Deep Packet Inspection. For example, your BitTorrent uploads and downloads might be monitored and limited by your ISP alongside services like Skype VoIP calls.
-
Providing additional security from pesky network admins at work. Did you know that many businesses have software on their network that lets your boss and/or IT guy know exactly what websites you are visiting, in real-time, as well as block access to other websites? If you've ever wondered why you can't browse Facebook or Twitter at work, that explains it. They are employing something like SonicWALL Traffic Monitor, BLOXX Internet Content Filtering, Exinda WAN Optimization or a number of other solutions. Setting up a VPN will let you bypass them in most cases. Although they will be able to tell that you're using a VPN and likely assume it's solely for the purpose of bypassing their monitors and/or if they are using something like Apple Remote Desktop they'll be able to see your screen, but I digress.
-
Access services limited by geographic region (ex: Pandora, Hulu, Spotify, BBC iPlayer)
Competitive Landscape
In the interest of writing an unbiased article, I wanted to point out that there are many VPN providers and VyprVPN is in no way the first mover in this space. Some have limitations. Some are free. Some are paid. Some are by known companies, and some look like fly by night operations. In no particular order, below are some other VPN providers, with their supported protocol types listed along the side.
- Cryptocloud (OpenVPN)
- WiTopia (PPTP, SSL)
- iPREDator (PPTP) (run by The Pirate Bay guys)
- Torrent Freedom (OpenVPN)
- Black Logic (IPSec)
- BananaVPN (PPTP)
- Perfect Privacy (PPTP, OpenVPN)
- StrongVPN (PPTP, SSL)
- AlwaysVPN (OpenVPN)
- AceVPN (OpenVPN, SSL, PPTP, L2TP)
- PureVPN (PPTP, L2TP, IPSec)
To be clear, I have not used any of the VPN providers in the list above. I just did some research and found them. I am not implying they are in the same class as VyprVPN, which boasts its speeds and network performance just as much as their customer service.
Setup...
Now that you have an idea of VyprVPN and other VPN offerings and their uses, let's proceed with installation and configuration. Since that all depends on your OS, I have gone through and written up install documentation with screenshots for Mac OS X 10.6, Windows 7, Ubuntu 9.10 and the iPhone.
Setup on Mac OS X (Snow Leopard)
Browse to Apple » System Preferences » Network and click the + icon found in the bottom left corner. In the drop-downs select VPN, PPTP and enter a service name of your choice, respectively, as shown below:
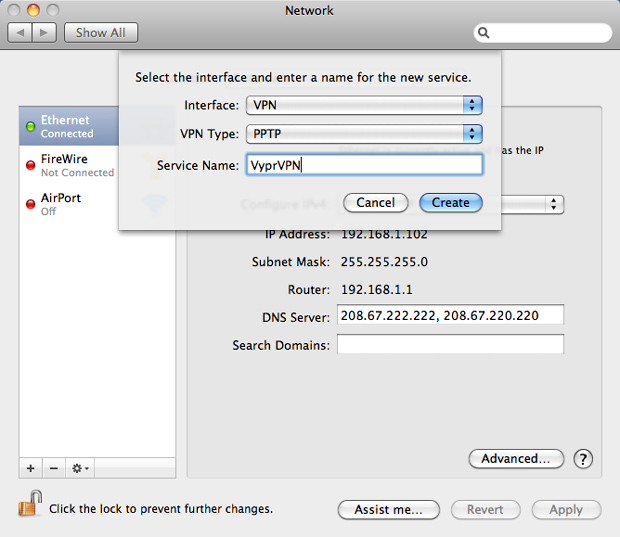 Adding a new VPN connection in Mac OS X
Adding a new VPN connection in Mac OS X
Click Create when done, then select the new connection in the left pane. On the right, enter one of the following for Server Address depending on which you live closest to:
- us1.vyprvpn.com (United States — Los Angeles)
- eu1.vyprvpn.com (Europe — Amsterdam)
Continue to fill out your VyprVPN username as described earlier for Account Name. You many optionally set Encryption to Maximum (128 bit only) instead of the default "Automatic (128 bit or 40 bit)" setting.
Click Authentication Settings and select the Password radio box. Supply your VyprVPN-provided password in that field and then click OK.
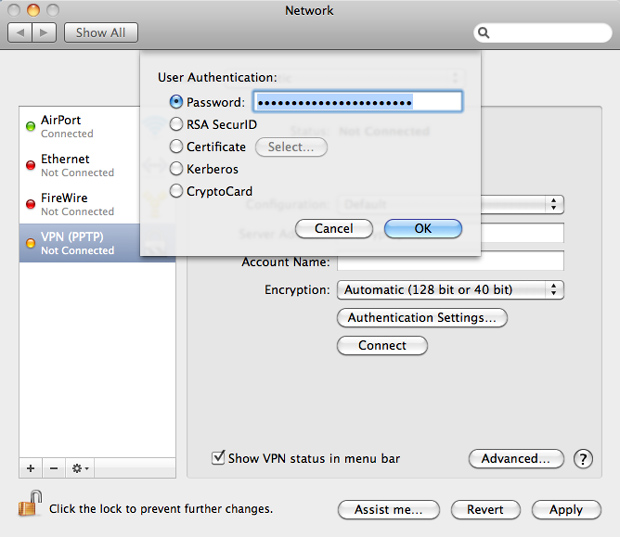 Set VyprVPN password - Mac OS X"
Set VyprVPN password - Mac OS X"
We're almost done! Click Advanced in the bottom right corner of the window and ensure that Send all traffic over VPN connection is checked. Click OK.
 Advanced VPN Settings - Send all traffic over VPN - Mac OS X
Advanced VPN Settings - Send all traffic over VPN - Mac OS X
Check Show VPN status in menu bar if it is not already. Click Apply then browse to the new, odd-looking VPN icon in the menu bar and connect to your new VPN.
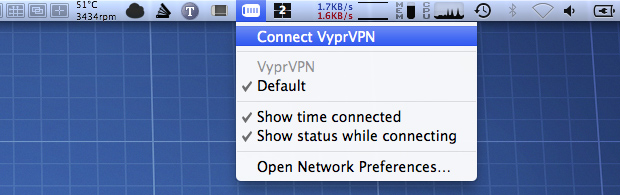 Connect to VyprVPN - Mac OS X
Connect to VyprVPN - Mac OS X
Disconnecting from the VPN connection can also be done by accessing the menu from that VPN icon in the menu bar.
Notes: OS X has a feature called VPN on Demand, listed as a tab on the Advanced page for VPN connections, that will theoretically automatically connect to the VPN when you attempt to access certain domains you provide. I say theoretically as I have tried many things to get it working without luck and have found users complaining about the same issue on Apple's forums. If/when this issue is fixed, it will be a great way to automatically ensure you are always on a secure connection when doing things like going to your webmail account and so on.
Also, if you would like to use a different DNS provider, like OpenDNS or Google Public DNS, than you use with your primary connection, you can specify that in the DNS tab in the same Advanced VPN options page. Otherwise, OS X will inherit any DNS servers you have set on your Ethernet or AirPort connection. It doesn't actually list those inherited DNS servers but I tested it and it still uses my OpenDNS configuration.
Setup on Windows 7
Fire up the Network and Sharing Center, most easily opened by clicking the Start button then using the search field to find it.
Under the "Change your networking settings" section, click Set up a new connection or network.
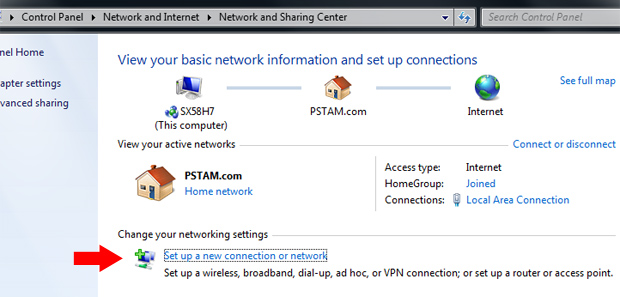 Set up new VPN connection - Windows 7
Set up new VPN connection - Windows 7
In the window that pops up, select Connect to a workplace. (If you already have another VPN connection, Windows 7 will ask if you want to use that connection. Select No, create a new connection and click Next.)
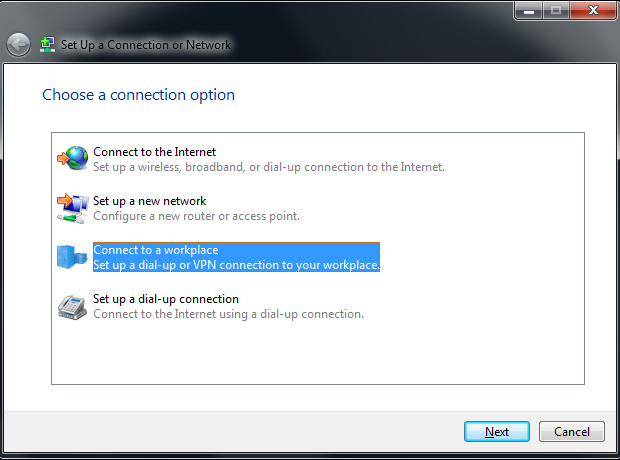
Click Use my Internet connection (VPN).

For Internet address, supply one of the following depending on which you live closest to:
- us1.vyprvpn.com (United States — Los Angeles)
- eu1.vyprvpn.com (Europe — Amsterdam)
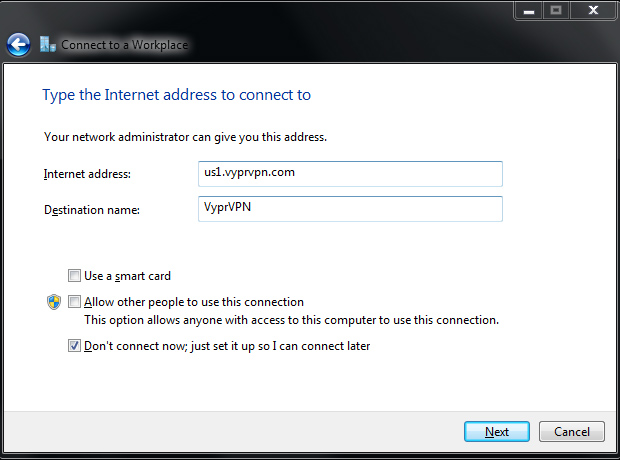
Provide a name for the new VPN connection, such as "VyprVPN", for Destination name. Click the checkbox for Don't connect now; just set it up so I can connect later, then click Next.
Type in your VyprVPN-provided username and password and check the box for Remember this password. Click Close
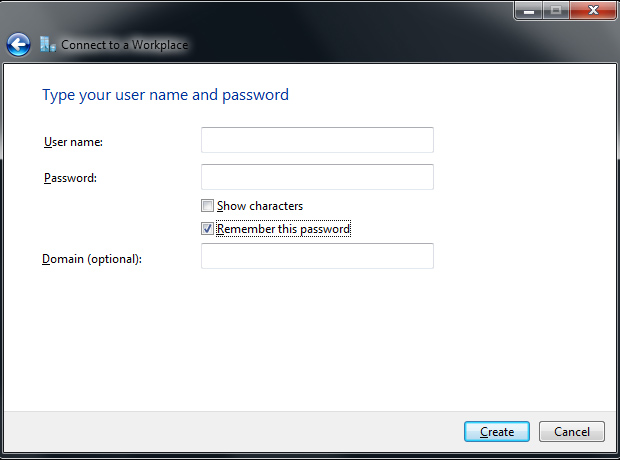
Click Close.
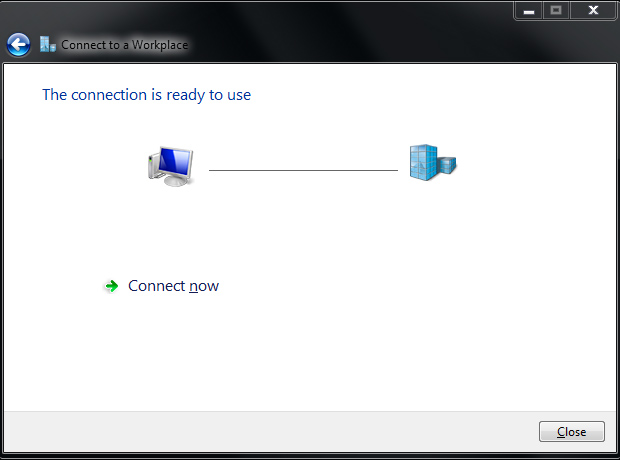
When you are ready to connect to VyprVPN, click the network icon found at the bottom right of your screen on the taskbar. A window displaying available networks to connect to will open up. Under the "Dial-up and VPN" section, your new VyprVPN connection will be listed. Select it, right-click and then click on Properties.
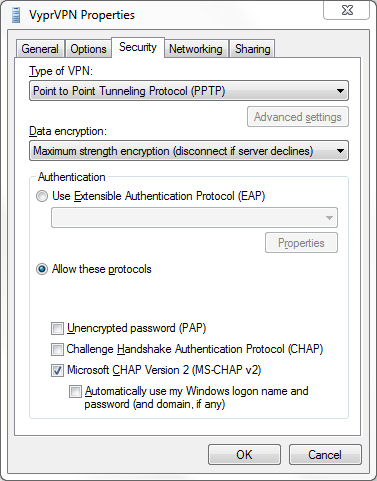
On the Security tab, set Data encryption to Maximum strength encryption (disconnect if server declines). Under the Authentication section, click Allow these protocols and under it uncheck all but Microsoft CHAP Version 2 (MS-CHAP v2). Click OK.
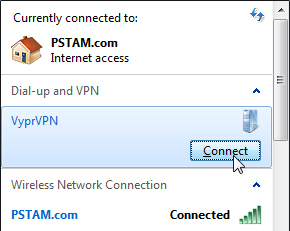
Go back to the network menu, select VyprVPN again and click Connect.
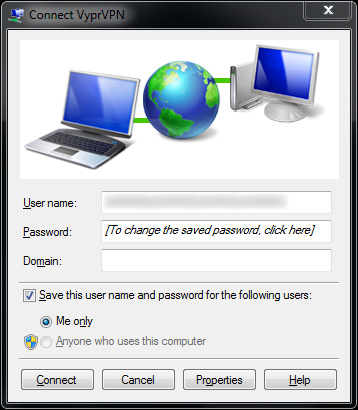
In the next window, click Connect as well. A few small connection status windows will show up and then you'll be successfully connected to the VyprVPN VPN service!
Disconnecting from the VPN can be done by clicking the network icon in the taskbar again, selecting the VyprVPN connection and clicking Disconnect.

Setup on Linux (Ubuntu 9.10)
Setting up a VPN connection is a bit more involved on a Linux box but for the better as you get easier access to some more advanced functionality. Start by browsing to System » Preferences » Network Connections » VPN.
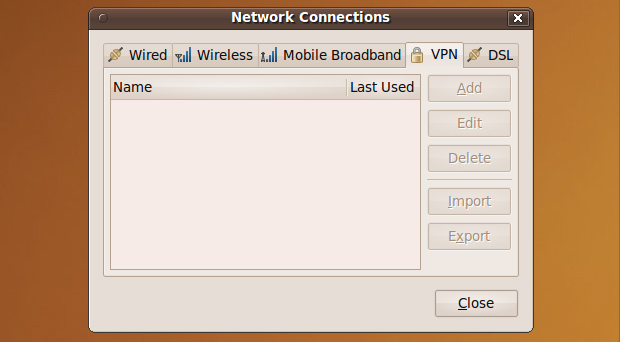
If you have never setup a VPN connection before there is a good chance that all the buttons, like "Add", are grayed out. Fix this by opening a terminal and running this command:
sudo apt-get install pptp-linux network-manager-pptp
Now go back to the Network Connections window and the VPN tab inside of it; the Add button should now be clickable. Click it, select Point-to-Point Tunneling Protocol (PPTP) in the drop-down and click Create.

Type something like VyprVPN in for Connection name. For Gateway, supply one of the following depending on which you live closest to:
- us1.vyprvpn.com (United States — Los Angeles)
- eu1.vyprvpn.com (Europe — Amsterdam)
Type in the VyprVPN-provided password and then click Advanced.
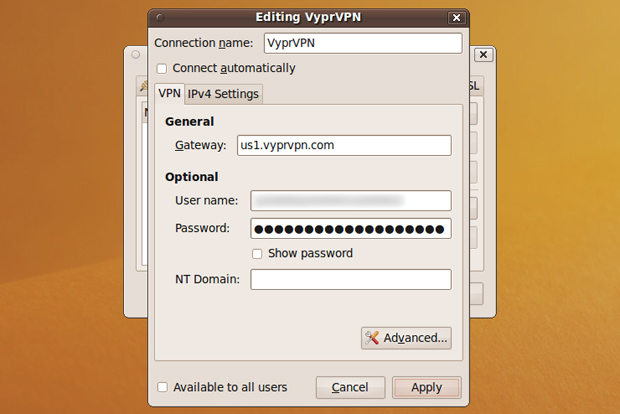
In the Authentication section, uncheck all but MSCHAPv2. More on why we're setting that at the end of this post.
In the Security and Compression section, check the box for Use Point-to-Point encryption (MPPE) and select 128-bit (most secure) in the drop-down below it. Then check the box for Allow stateful encryption and click OK and Apply.

If at any point during the VPN setup you see a keyring message like the one below, click Always Allow.
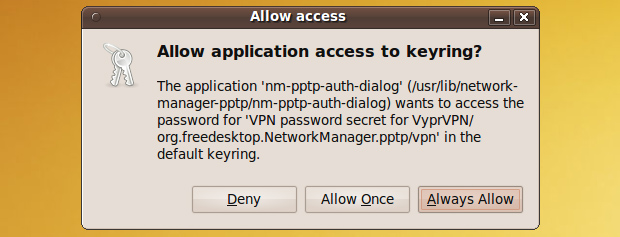
Restart the network manager by running this command in the terminal:
sudo /etc/init.d/network-manager restart
Now you are ready to take your new VyprVPN connection for a test drive. Click the network icon in the taskbar and click on your new VPN connection.
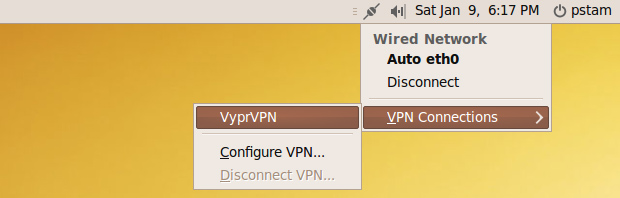
A few seconds later you should be successfully connected!
Setup on iPhone/iPod Touch
Browse to Settings » General » Network » VPN » Add VPN Configuration. Select the PPTP tab. Provide a name for the connection, like VyprVPN, in the Description field. For Server, supply one of the following depending on which you live closest to:
- us1.vyprvpn.com (United States — Los Angeles)
- eu1.vyprvpn.com (Europe — Amsterdam)
Type in your VyprVPN username and password in the Account and Password sections, respectively. Set Encryption Level to Maximum and toggle Send All Traffic to ON. Click Save.
Ensure that your new VPN connection is selected under the Choose a Configuration section. You can connect to your new VPN from this page or even more conveniently with the VPN toggle switch on main Settings page. Flip VPN to ON and it should connect shortly. VPN on the iPhone works with both 3G and Wi-Fi connections.
How do I know it's working?
Before connecting to your VyprVPN connection, find your IP address. There are many ways of doing this but you can easily find it by going to SpeedTest.net. Your IP will be displayed in the bottom left corner. Then connect to the VPN and refresh the page. Your IP should have changed and the map will now think you are in a different location.
Performance
As to be expected when routing your web traffic through another service, your throughput takes a hit in exchange for the extra security. How big of a hit depends on a few variables — where the exit server is vis-à-vis the servers of sites you commonly visit as well as the protocol used for creating the VPN connection. (It is a myth that VPN performance depends on having a nearby VPN server. It is more important that the VPN server is on the path to the servers of websites/services you commonly interact with.) That being said, PPTP is what VyprVPN uses and there are other more robust protocols for VPN connections. It is, however, the easiest to setup, manage and is natively supported by many operating systems (can be fast if properly configured because it's at the kernel level) right out of the box.
 Bandwidth tests with and without VyprVPN in various cities
Bandwidth tests with and without VyprVPN in various cities
How I Tested: The test box was a Windows 7 PC connected to the Internet directly with an Ethernet cable — no router in between (Once you go past 80 megabits my router doesn't route so well..). I fired up Firefox 3.5.6 with Flash 10.0.42.34 and went to SpeedTest.net. I did 5 tests at each location, with and without VyprVPN enabled and posted the best results from each. My Internet connection is a fiber line by DirecPath in Atlanta, GA.
As you can see, there is a noticable before and after difference in Internet bandwidth but nothing big enough to negatively change your typical browsing habits. The most important aspect is that download speeds remain high. The speed test at San Diego with VyprVPN enabled was the fastest of the VPN-enabled bunch because it is closest out-of-line location. Well actually, Los Angeles is where it exits but there is a bit of network congestion there. As the VPN-enabled speed tests get further away from San Diego, they naturally get a bit slower as they have to travel a further distance.
I should also mention that you can only connect to VyprVPN from one IP at a time, so using it simultaneously on your iPhone and laptop will not work; even if they are on the same router with the same WAN IP. I tried it and the new connection I made knocked off the other active VPN connection.
A Golden Frog Senior Engineer had this to say about speed tests, where they emphasize their support in helping customers optimize their speeds:
Speed tests are dependent on a number of factors such as the in-between network, home networking equipment, firewall and anti-virus software, and the speed-test location itself. One person's results can be very different from anothers just by changing something simple like wireless router firmware. Golden Frog's support staff will work directly with individual customers to get them the best speed for their specific conditions through their variety of network and troubleshooting options.
And here's a simple test on the iPhone:
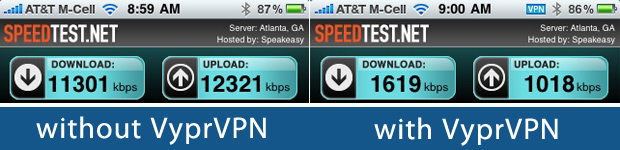 iPhone bandwidth test over Wi-Fi
iPhone bandwidth test over Wi-Fi
In Short: VyprVPN's network infrastructure is beefy enough to handle the needs of what you would do with a VPN — check email, surf the web, download files, consume content on sites that require a U.S. or European IP, et cetera. It would be nice to see VyprVPN add more VPN locations in addition to Los Angeles and Amsterdam.
Thoughts + Nerd Talk
In the beginning of this post I mentioned SSH tunnels. One of the problems with SSH tunnels is that if they are not configured properly your DNS requests will not go through the tunnel, easily exposing what websites you are visiting. While SSH tunnels and VPN, short for Virtual Private Network, achieve similar goals they operate at different layers of the OSI model (VPN PPP/PPTP at layer 2; compare to SSH at layer 7). VPN encrypts all traffic so you don't have to worry about properly setting up ports with any SSH tunnels. Encrypting all traffic with VPN does come at the expense of some network overhead but I do not think this will easily be realized with a personal VPN setup.
However, that same DNS request leak issue manifests itself with PPTP VPN connections if encryption is not enabled (side note: the PPTP protocol by nature implies no encryption or authentication — that relies on the configuration of the authentication methods. Keep that in mind when reading people online say that PPTP leaks DNS requests everywhere.. all depends on the config!). I tested my Linux VyprVPN setup by running it in a VM and then capturing the packets in the parent OS. The VM used a different IP than the parent OS, instead of the typical NAT/shared setup, so I could ensure that the data I was looking at was for the Linux traffic only. With my VyprVPN connection on my Linux box, no DNS requests got through (that's good!).
 Click for larger version. On the left you can easily see DNS requests coming through (bad!) and on the right is the properly configured VyprVPN connection that did not leak any DNS requests through.
Click for larger version. On the left you can easily see DNS requests coming through (bad!) and on the right is the properly configured VyprVPN connection that did not leak any DNS requests through.
Windows Users: Windows (XP, Vista, 7) has a DNS leak issue. Read about patching it.
MSCHAPv2 is the most secure authentication method that VyprVPN supports. CHAP, MSCHAPv1 and MSCHAPv2 are all similar protocols, with the latter two being Microsoft's implementation. They are all very old and vulnerable protocols. Security expert Bruce Schneier stated that with MSCHAPv2 "the fundamental weakness of the authentication and encryption protocol is that it is only as secure as the password chosen by the user." Keep that in mind and change the default password provided by VyprVPN to something much longer with lots of entropy (Notice: as of this posting, passwords cannot be longer than 8 characters but will be supported out of the gate when VyprVPN reaches its final release). As for other authentication protocols we are not using, EAP is more secure but I could not get it to connect to VyprVPN with that setting. There is also PAP, which you should avoid at all costs as it sends your password in plaintext.
While I'm on the subject of security here, it should be noted that there are still some latent vulnerabilities associated with using PPTP VPN instead of IPSec (albeit more complicated to setup, manage and more resource intense). As Schneier said:
Since authentication and key-exchange protocols which do not allow passive dictionary attacks against the user's password are possible - Encrypted Key Exchange and its variants, IPSec - it seems imprudent for Microsoft to continue to rely on the security of passwords. Our hope is that PPTP continues to see a decline in use as IPSec becomes more prevalent.
PPTP VPN connections can be compromised with man-in-the-middle and denial of service attacks that are protected against with IPSec VPN implementations. Examples of PPTP downgrade attacks were mentioned at the 2003 Black Hat Conference:
-
During negotiation phase
- Force PAP authentication
- Force MS-CHAPv1 from MS-CHAPv2
- Force no encryption
-
During re-negotiation (plaintext Terminate-Ack])
- Get passwords from existing tunnels
- Misc attacks
-
Force "password change" to get password hashes
- Hashes can be used directly by a modified SMB or PPTP client
- MS-CHAPv2 hashes not useful - force v1
Extra Reading If this technical aspect of VPN interests you, Microsoft actually has some great resources: VPN Tunneling Protocols, VPN Security, VPN Overview.
In Short: VyprVPN encrypts data and hides DNS requests when properly setup. Unfortunately, the underlying VPN technology used here is PPTP that is often scoffed at by security experts for being old and insecure. I would love to see the final version of VyprVPN (it is in beta now) ditch PPTP in favor of IPSec, L2TP over IPSec or OpenVPN protocols.
Verdict
If you are looking for an extra bit of security while checking your email at the local coffee shop where you frequently work then VyprVPN is just what you're looking for. It's easy to setup and provides a sufficient layer of extra security. If you are trying to use the hotel Wi-Fi connection while attending Def Con, I do not recommend using VyprVPN or else your login information will end up on their wall of sheep. In that case you would want to find an OpenVPN, SSL or IPSec VPN provider.
VyprVPN is currently in beta and only available to Diamond level customers of Giganews until June 2010. They state the value of VyprVPN is 14.99 per month, so it can only be assumed that it will cost that much if and when it is offered on its own. Compared to other VPN providers this seems to be on the higher end of the scale in terms of pricing, assuming the others which I have not tested offer similar speeds. Combined with PPTP, VyprVPN will make for a hard sell for the utmost security minded folks. I hope VyprVPN will offer an OpenVPN service in the near future. This is what a Golden Frog Senior Engineer had to say when I asked them about future offerings:
We aim to be competitive with existing offerings in the space and are focused on not just providing the same kinds of VPN service, but VPN service focused on speed and reliability.
Hopefully by reading this article you have learned a few things and know how to shop for a VPN provider should you need one in the near future. The most important things to look for in a VPN provider are as follows: a secure protocol like OpenVPN or IPSec, a Privacy Policy and Terms of Service that aligns with what you plan on using that service for, a reasonable bandwidth allowance and servers near the sites you access (in general - if you live in the U.S. and visit U.S. sites often, a VPN provider with a U.S. location will suffice). Properly configured PPTP VPN connections are okay for adding a bit of security — enough to foil any random running a packet sniffer for their first time — but for anything important, avoid them:
IPREDator co-founder Peter Sunde, who also founded popular file-sharing site The Pirate Bay, told iTnews: "128-bit encrypted PPTP can probably be broken by someone that can eavesdrop on the traffic." iTnews - Pirate Bay's IPREDator not a place to hide
VyprVPN gets 7.5 out of 10 Stammys with casual web surfers in mind, great support and a fast connection. The security-minded nerd side of me cannot score a PPTP VPN connection higher than that.
How do you currently browse the web when on untrusted, open networks? Have you ever used a VPN for the purpose of keeping your data safe or bypassing some ISP traffic shaping/etc limitations? Is VyprVPN something you would pay for?
Disclosure: I have a been a paying customer of Giganews since early 2008. Giganews bought me lunch at South By SouthWest Interactive last year and it was tasty. This post was not paid in any way, shape or form. I find this stuff interesting on my own and figured it would make for a great review. Some links in this post utilize an affiliate tag, which helps pay for some of my startup and living expenses as well as student loans.
Please leave a comment if you have enjoyed this post! Follow me and my nerd musings on Twitter and FriendFeed.