Last week I boasted about the release of PGP Whole Disk Encryption for Mac OS X and how it is definitely something to consider if data privacy is of utmost importance to you. By encrypting my hard drive, I am able to keep all of my data safe from physical disk access and other such tampering. Since publishing that post I have installed and been using PGP WDE on my MacBook Air for about a week.
Installation and Configuration
Setting up PGP WDE had quite a few steps but was a pretty smooth process overall. After installing the actual PGP Desktop application, I was led through creating and publishing a PGP key. When that was done, it was time to embark on the task of actually encrypting my hard drive.
PGP Whole Disk provides the next level of security and convenience by encrypting your entire disk. The encryption process can be lengthy, however PGP desktop runs in the background. You may also pause and resume the process at your convenience.
All I had to do was select my hard drive, provide a passphrase and it began encrypting my hard drive. As the snippet above explained, PGP WDE encrypts in the background, unlike Apple's FileVault which locks you out for hours while it encrypts. The entire encryption process took about 2.5 hours on my 1.6GHz MacBook Air, which had 55GB of data in use.
In Pictures: PGP WDE Setup
 Setup PGP Keyring
Setup PGP Keyring
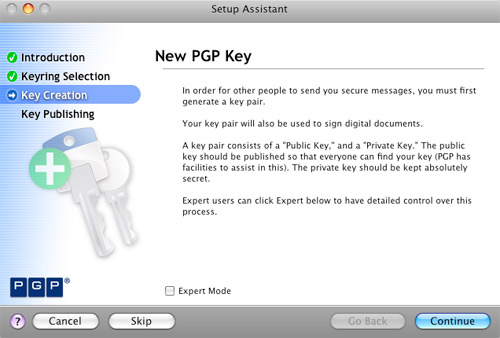 Create New PGP Key
Create New PGP Key
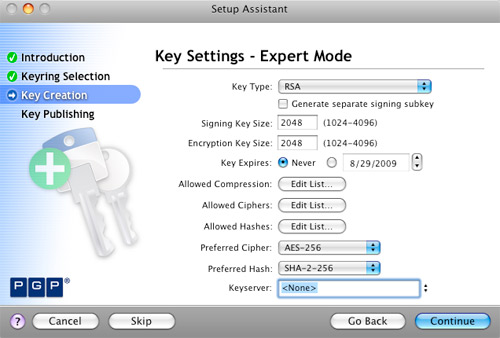 PGP Key Settings - Expert
PGP Key Settings - Expert
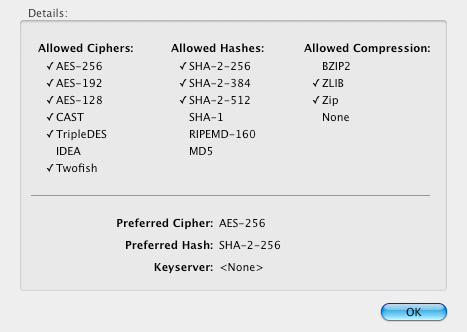 PGP Key Support Settings
PGP Key Support Settings
 PGP Key Passphrase
PGP Key Passphrase
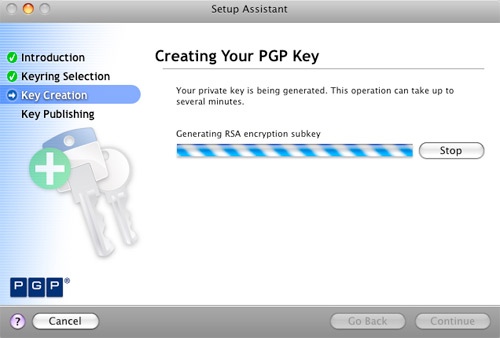 PGP Key Creation
PGP Key Creation
 PGP Key Creation Summary
PGP Key Creation Summary
 Publish PGP Key
Publish PGP Key
 Disk Encryption Main Page
Disk Encryption Main Page
 PGP Encrypt Whole Disk
PGP Encrypt Whole Disk
 PGP Whole Disk Encryption - Add User
PGP Whole Disk Encryption - Add User
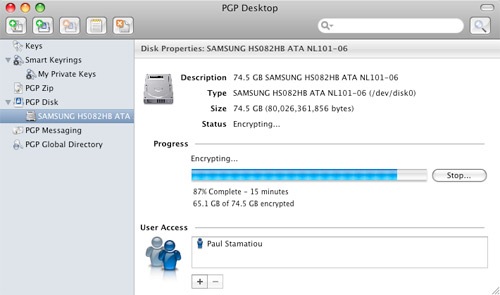 PGP Whole Disk Encryption Process
PGP Whole Disk Encryption Process
 PGP Whole Disk Encryption Complete
PGP Whole Disk Encryption Complete
Performance
The first question I get asked when people find out that my hard drive is encrypted is how the performance of my computer is affected with the constant encryption/decryption process going on in the background. I'm pleased to report that I have not experienced any negative, discernible performance issues. It feels exactly the same as before I installed PGP WDE.
Likewise, PGP WDE has not affected my workflow at all. No PGP application needs to be open during normal use. From the in-OS standpoint, you would never know that the hard drive was encrypted. It's when you turn on the computer that you're faced with a pre-boot authentication screen.
 Pre-boot Authentication
Pre-boot Authentication
In addition to the PGP key created during setup, a passphrase protects the computer at login. That being said, it's important to pick a lengthy password with lots of entropy. For example, to take full advantage of AES 256-bit encryption you must supply a 64-character passphrase. Otherwise, the passphrase will be the weak link in your hard drive's security, not the PGP keypair. Unfortunately, two-factor authentication, such as having the passphrase and a smart card/USB token, is not supported in WDE for OS X.
Additional OS X Security
My only complaint with PGP WDE is that passphrase authentication is not activated when waking the computer from sleep. That means that my laptop is most vulnerable when waking from sleep. Granted, it is still protected by OS X's own password system.
 OS X Login Keychain Settings
OS X Login Keychain Settings
That's why I changed my login keychain settings to lock when sleeping. That means that even if someone gains access to the system, they will not be able to use any applications that rely on login and password info stored in the OS X login keychain. That includes applications like Adium and Transmit.
More Security Paranoia
A common attack to gain access to encrypted hard drives is the cold boot attack where an attacker exploits a hardware vulnerability in RAM to find encryption keys, and then use those keys to decrypt the hard drive. I contacted PGP about this possibility and they told me that "it is stored on the MBR encrypted with AES-256."
With PGP WDE, your encrypted hard drive is safe from cold boot attacks but that doesn't mean someone can't find other data in your memory - if your memory is removable. PGP WDE's pre-boot authentication will prevent someone from rebooting your machine and booting up a live, lightweight Linux distro (such as BackTrack, Auditor, PHLAK and Knoppix-STD) that won't disrupt the memory footprint too much and make data recovery from your memory a reality. The MacBook Air has soldered-in RAM chips: horrible from an expansion standpoint, but great from a security standpoint.
 Me with a 185 liter dewar of liquid nitrogen.
Me with a 185 liter dewar of liquid nitrogen.
With soldered-in RAM, people won't be able to cool your memory with liquid nitrogen (as above) to retain data longer, remove it from your pre-boot authentication-secured system, put it in their computer and copy the contents of the memory before it heats up and flips all the bits. That's just a long way of me saying that the MacBook Air is fairly secure from the hardware perspective. Even more so if you have a Solid State Drive in it. I digress, but SSDs are notoriously bad when it comes to data recovery; that is, bad for you if you legitimately want to recover your data, but good for you when your computer is in the hands of attackers.
The algorithms which map addresses to physical media locations vary from manufacturer to manufacturer - and in many cases - like the formula for making Coke or Pepsi - the details are closely guarded commercial secrets. Data Recovery from Flash SSDs?
 RAM chilled with any coolant, such as liquid nitrogen, retains data much longer and makes it easy for cold boot attackers to copy the contents of the RAM for snooping. Without cooling, RAM forgets data within 2 minutes.
RAM chilled with any coolant, such as liquid nitrogen, retains data much longer and makes it easy for cold boot attackers to copy the contents of the RAM for snooping. Without cooling, RAM forgets data within 2 minutes.
For general protection from cold boot attacks, I recommend turning off your computer when you are in situations that it is possible for someone to gain physical access to your machine, in addition to setting your Mac to hibernate mode 0.
Other PGP Desktop Features
In addition to whole disk encryption, PGP Desktop provides a slew of security-oriented features. Notable features include encrypted zip files, secure email and AIM messaging and my favorite, PGP Shred. PGP Shred securely deletes anything you want and depending on your settings, can exceed the Department of Defense's 5220.22-M media sanitization requirements, also known as NISPOM. It's not as entertaining as popping CDs in the microwave when the Feds are knocking, but it gets the job done.
Speaking of the Feds, the Federal Trade Commission recently launched OnGuard Online, a site providing consumers tips on protecting themselves from online fraud and securing computers.
Thoughts
PGP Desktop's support for Whole Disk Encryption for Mac OS X is a user-friendly security sidekick. It does not involve changing the way one works with their computer nor does it affect performance. (By the way, PGP WDE does not work with BootCamp). While WDE for OS X does not yet support enterprise-level security in the form of two-factor authentication, it is still highly effective in promoting data security. PGP WDE receives 10 out of 10 Stammys.
Disclaimer: My reference to the United States government as the "Feds" is entirely tongue-in-cheek and pop culture based, not intended to be derogatory or negative in any way, shape or form. Don't sue me, I'm not Jon Lech Johansen (the guy who cracked DVD CSS and whose blog was once entitled "So Sue Me").
Is PGP WDE right for you? How do you keep your data secure?
Update 12-3-08 After having used PGP WDE on a faster computer with an SSD, I began to notice that with WDE enabled, the reads and writes were considerably slower. So I ran a few benchmarks and discovered that this was in fact the case - up to 4 times slower.