Part 3: Azureus Anonymity
Note: Please consider setting up a Tor server to donate bandwidth to the network.
 There has recently been a lot of buzz about decentralized trackers for BitTorrent and other tools resulting in anonymous filesharing. My goal for this article is to have your Azureus installation running on the Tor anonymizing overlay network for TCP. I will essentially be translating this article into something that you can follow. This article is part of a series, please check out the first and second articles if you have not done so already. Warning: This one's a bit more difficult.
There has recently been a lot of buzz about decentralized trackers for BitTorrent and other tools resulting in anonymous filesharing. My goal for this article is to have your Azureus installation running on the Tor anonymizing overlay network for TCP. I will essentially be translating this article into something that you can follow. This article is part of a series, please check out the first and second articles if you have not done so already. Warning: This one's a bit more difficult.
So what exactly is Tor?
Tor is the tool we are going to use to provide a layer of anonymity to Azureus. There is another approach to anonymous Azureus using the I2P network and you may attempt that by yourself. With Tor, your data takes a random route using Onion routers, a distributed network of servers, rather than a direct source to destination path. You can think of Tor as a large network of proxies. Your data randomly hops from proxy to proxy until it reaches its destination. That being said, anonymity is not the fastest thing so don't expect to be getting 600kb/s down. This makes it impossible for anyone to find out any more information about your packets than where they are traveling to at a specific point and since Tor makes sure your data travels in random paths, you are safe. The Tor network is still in its infancy so it is important to understand that we will not be routing peer-to-peer traffic through it, merely client and tracker configuration data. Also, if you're feeling adventurous you can setup Tor for many online-enabled programs.Now what?
 Point your browser over to the Tor download page and get the latest version of Tor for your OS. Keep your browser on that page and click the Tor installation instructions for either Windows or Mac OS X. Those pages may look intimidating, but we will be skipping the part that says "Configure your applications to use Tor." If you are following this for Windows, make sure to download and install Privoxy. All you need to do at this point is install the essential Tor package, no need to configure Privoxy just yet.
Point your browser over to the Tor download page and get the latest version of Tor for your OS. Keep your browser on that page and click the Tor installation instructions for either Windows or Mac OS X. Those pages may look intimidating, but we will be skipping the part that says "Configure your applications to use Tor." If you are following this for Windows, make sure to download and install Privoxy. All you need to do at this point is install the essential Tor package, no need to configure Privoxy just yet.
Choosing a Configuration
Azureus and Tor can be configured to allow for several different types of Azureus usage. You can choose from an anonymous tracker server, anonymous client, anonymous tracker client, anonymous outbound/inbound peer traffic with a public tracker, or anonymous peer data with an anonymous tracker. Since I am pretty sure that most people reading this article are just regular Azureus users and don't host a tracker server I'm going to go forth with the anonymous client.
Down and Dirty
Open up Explorer/Finder and find your way to C:/Program Files/Privoxy or /Library/Privoxy respectively. Open config.txt in Notepad/TextEdit or your favorite text editor. To this we will add these this line to the very top, before the comments:
forward-socks4a / localhost:9050 .
Then, use the search function and find these two lines:
logfile privoxy.log
jarfile jar.log
In front of each line, place a # to comment them out. Do not forget to save this file.
The next config file we are going to edit is the one used by Tor, torrc. You can find it in C:\Documents and Settings[USER NAME]\Application Data\Tor or by navigating to Start>Programs>Tor>torrc. Once you've located this file, open it up in a text editor and add the following two lines to the top like we just did:
HiddenServiceDir C:\Program Files\Tor\bttracker
HiddenServicePort 6969 127.0.0.1:10069Note: If you are running Mac OS X you will have to change C:\Program Files\Tor\bttracker to /Library/Tor/bttracker and create the directory bttracker in /Library/Tor/. Make sure to save this file.
Now go to C:\Program Files\Tor</strong> and create a directory called bttracker.
Almost There
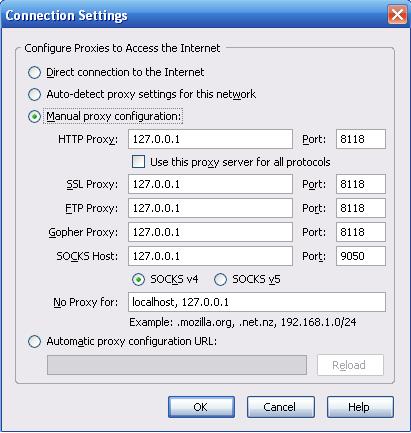
Exit both Tor and Privoxy if they are open, and restart them. This will allow the changes we made in their config files to take effect. If you navigate to C:\Program Files\Tor\bttracker or /Library/Tor/bttracker, there should be two shiny new files just created, hostname and private_key. Right click on hostname and open it in a text editor. There should be one line of text, copy it. For reference, mine was u6sybfzer6icp5mt.onion. This is your tracker's address. Fire up Azureus and paste this into the first field in Options>Tracker>Server that should be labeled "Tracker external IP address." While still on this options page, scroll down until you find a checkbox marked "Enable compact announce protocol," uncheck it. Go to Options>Connection and check the boxes labeled "Enable proxying of tracker communications" and "I have a SOCKS Proxy." For "Host" enter localhost and for "Port" enter 9050. Click "Save." You may now close the Options. Restart Azureus for the changes to take effect.If you want to be able to see the tracker in your browser, click the make a torrent icon in Azureus and click the "Use an external tracker" radio button. The field below it should have your the address you're looking for. You won't be able to access *.onion addresses unless your browser has the proxy properly setup. Consult the Tor installation page again for setting up your browser. However, all you really need to know is to use 127.0.0.1 and port 8118 for every service. You can test your proxy by accessing this wiki page http://6sxoyfb3h2nvok2d.onion/tor/.
It is also a good idea to visit showmyip.com to make sure that it displays a different IP address than your real IP. That is a sign that Tor and Privoxy are doing their jobs. I highly recommend you browse around the Internet while on Tor to get a feel for the kind of speed Tor currently has. It is far from speedy. I am not promoting the use of bittorrent on the Tor network, merely showing you how to do it strictly for informational purposes. The last thing I want is to get flamed for abusing the Tor network.
As Steve Jobs says, "One More Thing..."
If you are running from behind a router, you will have to take the necessary actions to open up the ports used by Azureus, Tor, and Privoxy. Check article two if you are not sure how to forward ports in your router. You should be set if you open up 8118, 9050 and 6969, assuming default ports are used. I highly recommend setting up Tor and Privoxy not behind a router first to make sure that is setup correctly, and then putting it back behind the router and seeing which ports need to be open. Just a trial and error kind of thing.

That's It! I only recently found out about the Tor network and researched it until I was able to come up with this article. I hope this article was helpful, at least to some people.